RBAC (Roled based access control) is a security feature used to control access based on user roles in an organization, that is, considering its functions within the organization. In large organizations is a classic way to organize permits, based on the competences, authority and responsibility of a job.
A RBAC attribute is the dynamism, because the access control function is given to a role and integration in that role of a person can change over time, like the permissions associated with a role. It is opposed to classical methods of access where access permissions are granted or revoked to a user object to object.
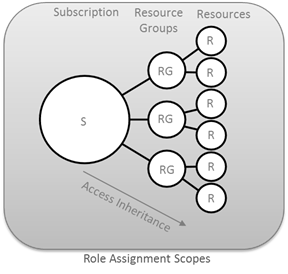
In AZURE we have a RBAC implementation for resources and a number of predefined roles. The roles in AZURE can be assigned to users, groups, and applications, and at the level of subscriptions, resource groups, or resources. As we see the options are vast.
There are three basic roles: owner, contributor or partner, and reader. The owner has full access to resources, including permissions to delegate access to others. The contributor is equal to the owner but can not grant access to others. The reader can only see resources.
Of these three roles inherit another set of roles for specific resources. In this link is a full list of roles based on Azure and its functions.
However you can generate as many roles with custom permissions as necessary. To create them can be done via Azure PowerShell, Azure client line interface (CLI), or the API REST. In this link you have more information and examples of how to do it.
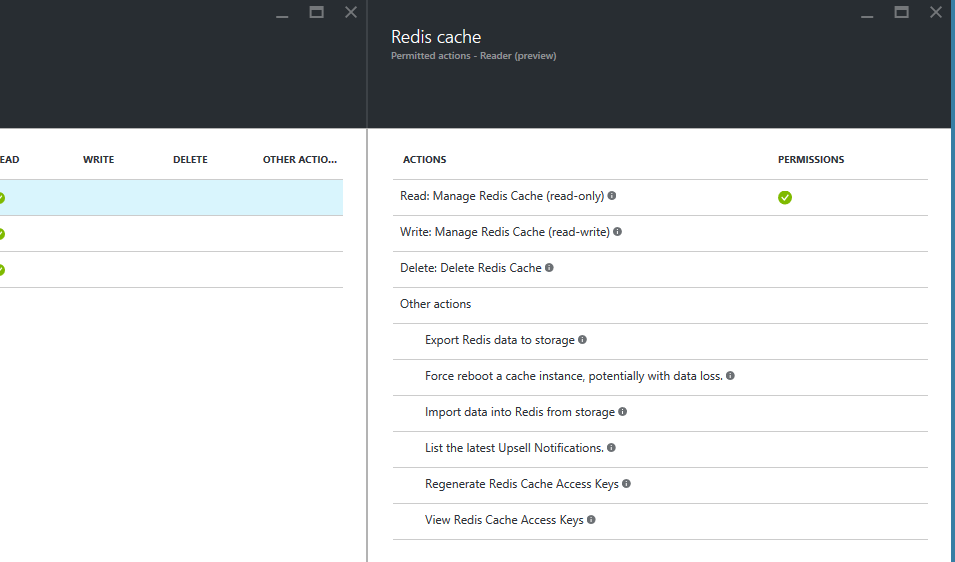
Access to the list of permissions for each role
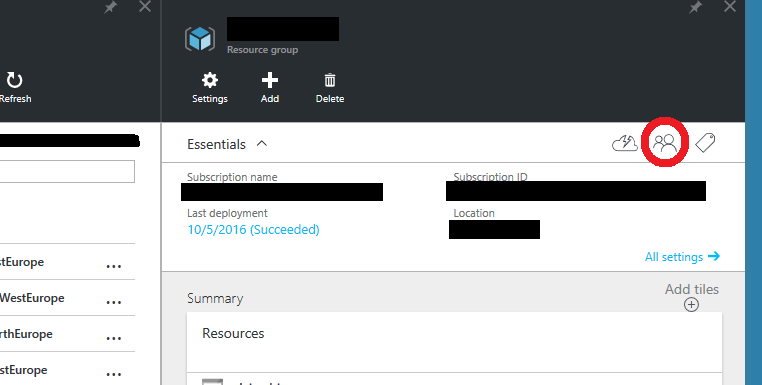
One way to check what permissions each role have, is through the portal AZURE. You enter into a subscription, resource group or resource, and you will see an icon like two peoples at the top right:
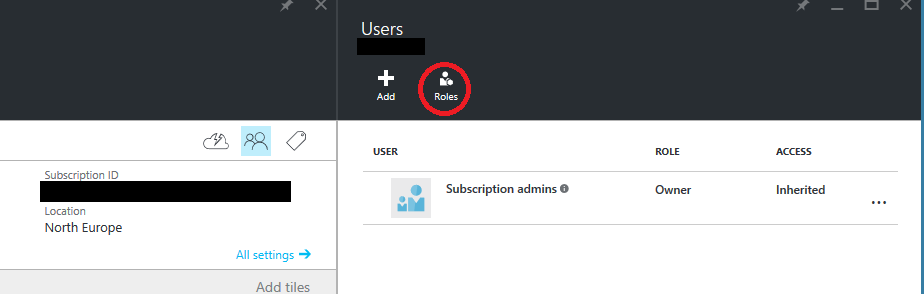
Selecting it, the users panel appears. Click Role:
And the list of available roles will appear:
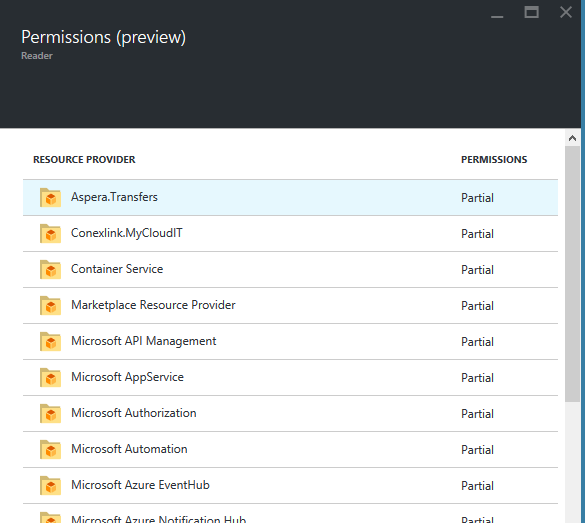
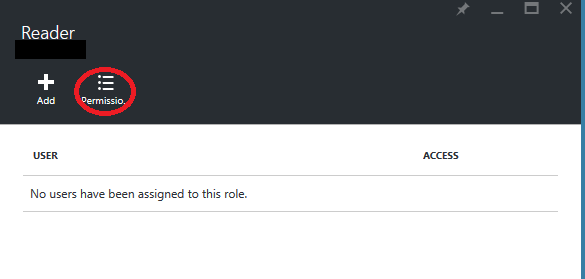
Select the role that interests you to check their permissions, and the Members Role tab appears with a button to see the list of permissions:
 Once on the list we can expand information for each group of actions by clicking on the corresponding entry:
Once on the list we can expand information for each group of actions by clicking on the corresponding entry:
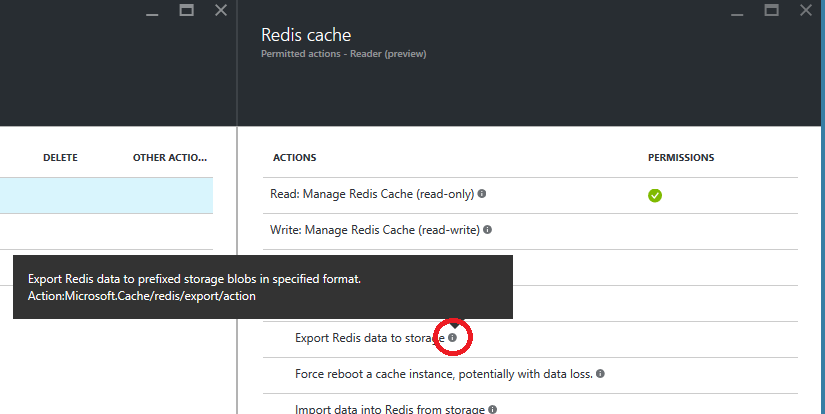
And within it each individual action:
At this level is useful the information that provides the icon to learn more on each input with an explanation of each share representing:
To learn more about how to create, delete or consult the members of each roles, you can consult the following link.